Registration Dashboard
Welcome to the Registration Dashboard! This page provides insights into SIP registration activity, trends, and security. Use the tabs below to explore each metric in detail.
- Events Over Time
- Parallel Regs
- Registrations Map
- Top Types Count
- User-Agents in Reg. New
- Transport Protocol
- Top Reg. Expired
- Registration Events
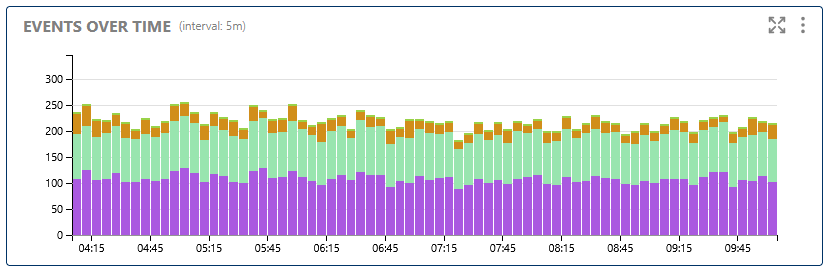
This chart displays the number of registration events (such as new, expired, and deleted) over time. Monitoring these trends helps you quickly spot unusual activity, registration storms, or service interruptions.
Shows the number of registration events (new, expired, deleted) over time to help monitor system activity and detect anomalies.
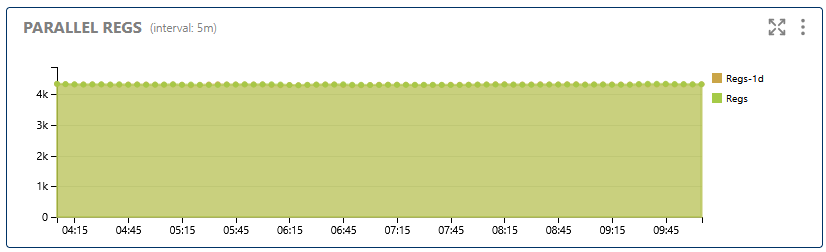
This section shows the number of endpoints (phones, gateways, etc.) that are registered at the same time. High numbers may indicate peak usage, while sudden drops could signal outages or mass disconnects.
Displays the number of simultaneous SIP registrations, indicating endpoint activity and system load.
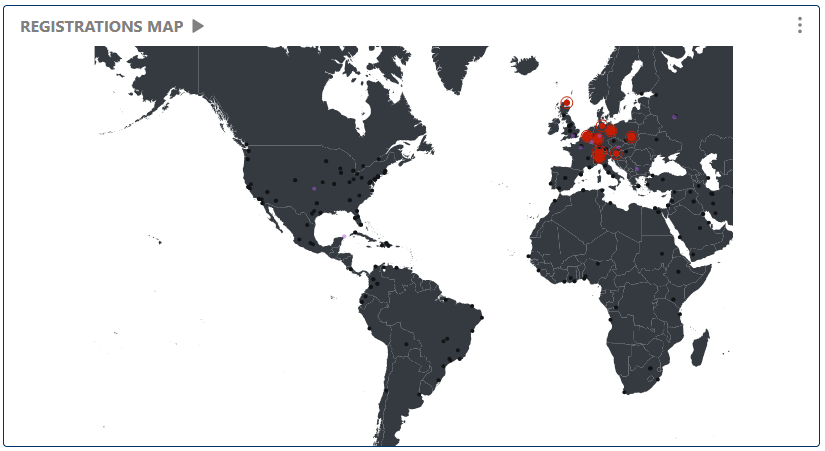
The map visualizes where registrations are coming from geographically. This helps you identify regional usage patterns, spot unauthorized access from unexpected locations, or monitor global service reach.
Visualizes the geographic distribution of SIP registrations, helping to spot regional trends or suspicious activity.
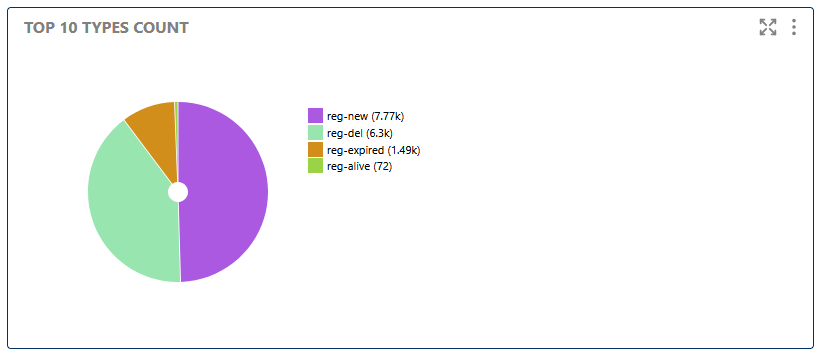
Here you can see which registration event types (new, expired, deleted) are most common. This is useful for quickly assessing system health and identifying abnormal behavior, such as a spike in expired registrations.
Shows the most frequent registration event types, such as new, expired, or deleted, for quick analysis of system behavior.
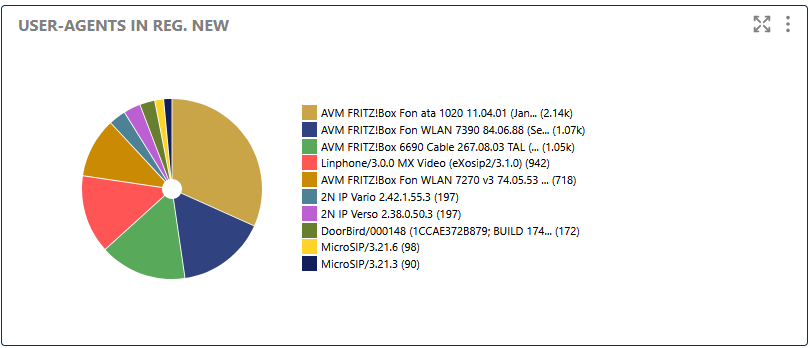
This section lists the most common SIP User-Agents (phones, softphones, apps) seen in new registrations. It helps with device inventory, firmware tracking, and detecting unknown or suspicious devices.
Lists the most common SIP User-Agents seen in new registrations, useful for device inventory and anomaly detection.
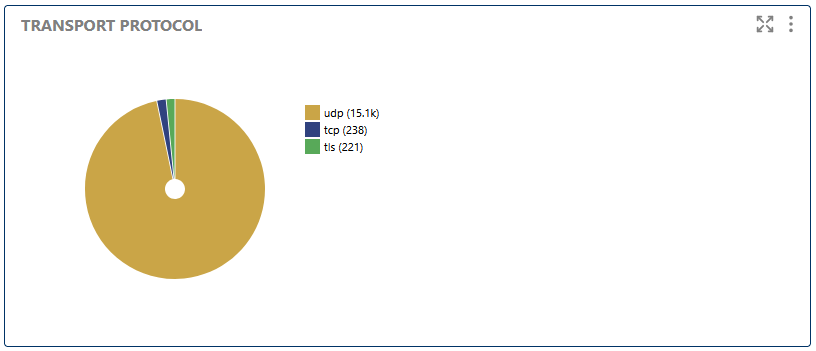
Here you can see which transport protocols (UDP, TCP, TLS) are used for registrations. Monitoring protocol usage helps with network planning, security enforcement, and troubleshooting connectivity issues.
Breaks down registrations by transport protocol (UDP, TCP, TLS), helping to monitor security and network usage.
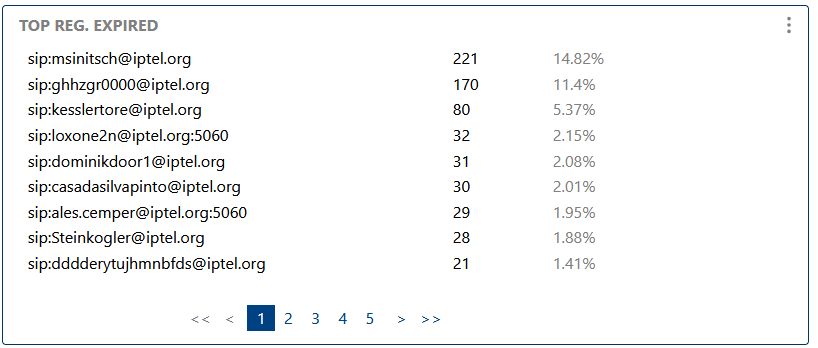
This section highlights endpoints or users with the most expired registrations. Frequent expirations may indicate network problems, misconfigurations, or even security attacks (like registration floods).
Highlights the endpoints or users with the most expired registrations, which may indicate connectivity issues or attacks.
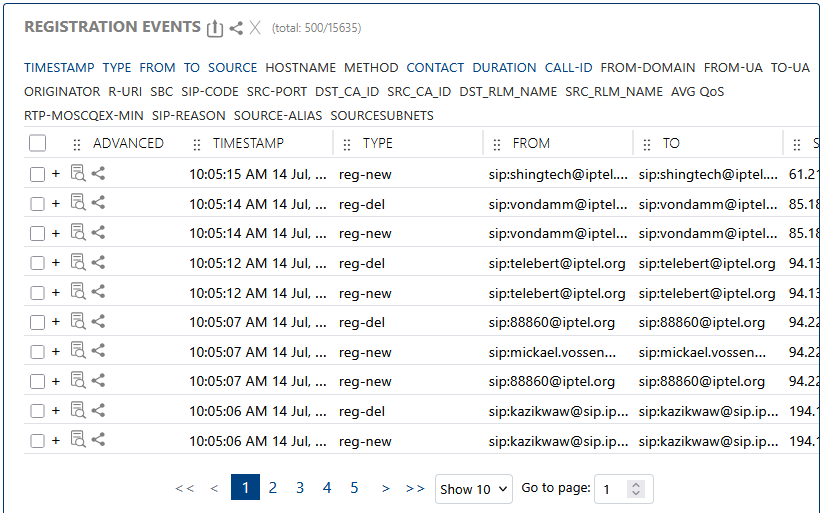
This tab lists individual registration events with detailed information for each. Use it for troubleshooting, auditing, or investigating specific registration scenarios.
Lists individual registration events for detailed inspection and troubleshooting.